‘Anonymity does better when it accompanied with awareness and education’ says Ahmado (2014). Ahmado hides her/his identity as an activist inside Syria, but at the same time admits that this anonymously doesn’t protect its holder from been revealed by a malware or hackers attacks.
In this regard, Ballard (2014) reported that Iranian government is working to block the internet anonymity. ‘It is believed that by preventing anonymous browsing, it hopes to deter individuals from posting contentious content.’
According to Najem (no date), most of Arab government doesn’t have a specific law of anonymity online as right, contrary; it might prosecute under a terrorism law. Saudi Arabia and Kuwait are among other Gulf Cooperation Council countries that potentially may follow.
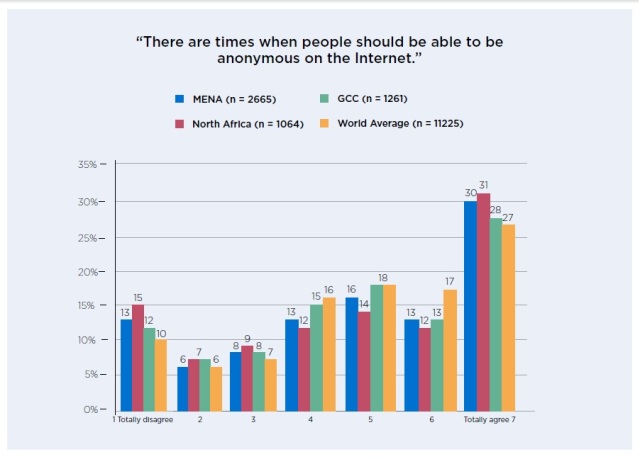
July 2014 survey of the ministry of Information and Communications Technology (ICTQatar) on the attitudes of online users in MENA region to cyber safety, security and data privacy, revealed that 30% of internet users in Middle East and 31% of North Africa tend to “totally agree” the right of being to occasional anonymity online whereas this percentage considered 3% above the world average (please refer to the figure below).
This result indicates that there a trend in MENA to use anonymous identities due to internet privacy fears and its citizen suspicions prospect towards their communications especially after Snowden leaks which confirmed to what extent governments are spying, collecting and processing personal data to analyze individuals’ behaviors.
Despite the fact that MENA Internet users are ‘most likely to express an opinion about politics online’ with their real names, the survey demonstrated that they are ‘more cautious about what to say and does online.’
Earlier, in 2011, International Business Times reported that the Free Software Foundation awarded Tor Project for protecting Anonymity in Libya. Tor Project went on use broadly during Turkey’s 2014 March protest when the authorities banned Twitter, says AlHussaini (2014). It offers considerable privacy margins to its user’s identity, location and login tracking.
Wikileaks founder suggests whistleblowers to use Tor as safe transporter, Russia offered four million rubles to crack the project (Rothrock, 2014), while NSA described people who use Tor as “Very naughty people” (Coursen, 2014).
This post was originally prepared as part of HIVOS INTRODUCTION TO INTERNET GOVERNANCE 1410 (B), FINAL ASSIGNMENT.

